Today’s data environment is stacked against you
Sensitive data is everywhere
Data sprawl makes it harder to find and secure what matters, especially sensitive data.
Shadow data escapes detection
Unknown, untracked data create blind spots that legacy tools simply can’t account for.
Regulations outpace control
Regulations evolve quickly, outpacing static tools and creating unseen compliance gaps.
An identity-centric approach to data security
We connect data to the people it represents, securing sensitive data, protecting privacy, and reducing risk in real time.
Your data isn’t just files. It’s people, context, risk.
Our platform maps structured and unstructured data to business context and human identity, then automates protection, governance, and privacy.
- . Discover and map sensitive data to identities
- . Enforce access and governance with precision
- . Automate privacy workflows and compliance
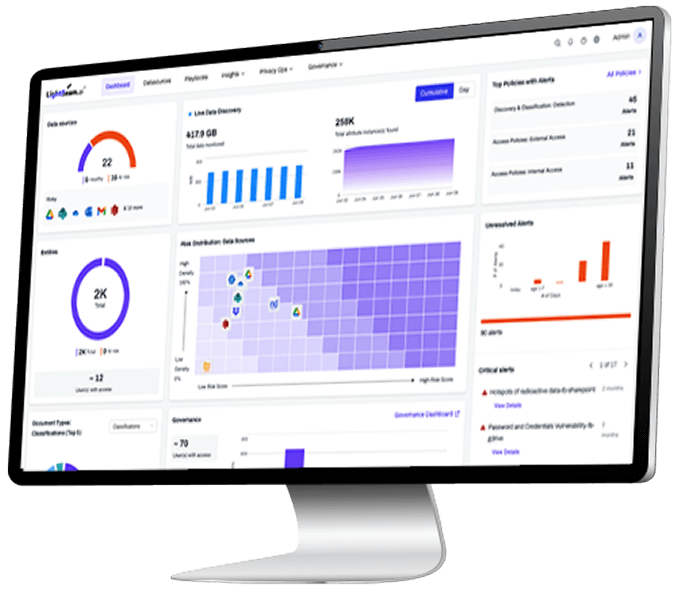
Scan for Sensitive Data
Lightbeam scans structured, unstructured, and semi-structured sources to uncover hidden sensitive data across your cloud, SaaS, and on-prem environments.
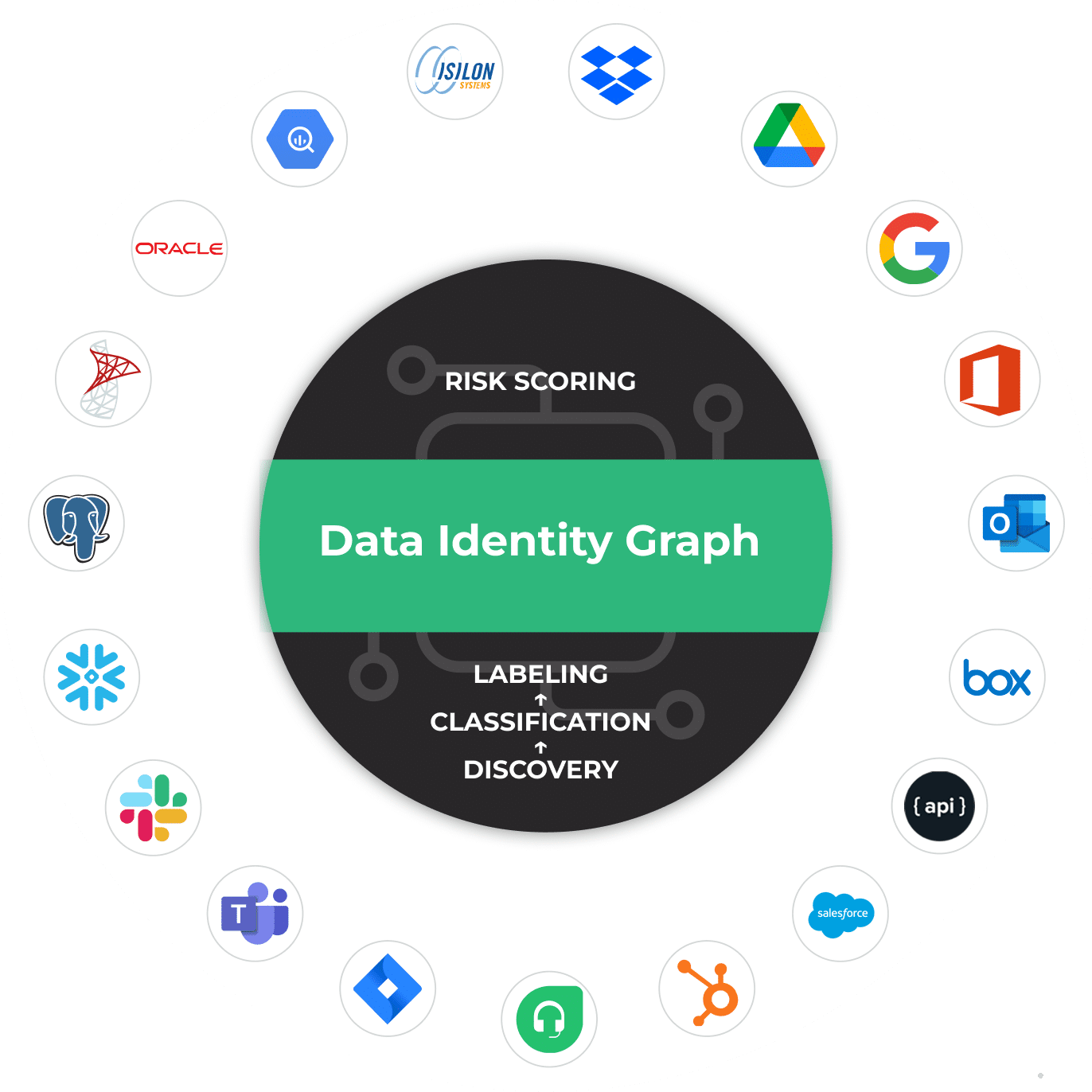
AI-Powered Data Identity Graph
Using its Data Identity Graph, Lightbeam classifies sensitive data, maps it to people, applies labels, and scores risk for focused remediation.
Automated Risk Reduction at Scale
Lightbeam applies AI-driven remediation across data security use cases like DLP, DSPM, and breach protection, reducing risk at scale.

Scan for Sensitive Data
Lightbeam scans structured, unstructured, and semi-structured sources to uncover hidden sensitive data across your cloud, SaaS, and on-prem environments.

AI-Powered Data Identity Graph
Using its Data Identity Graph, Lightbeam classifies sensitive data, maps it to people, applies labels, and scores risk for focused remediation.

Automated Risk Reduction at Scale
Lightbeam applies AI-driven remediation across data security use cases like DLP, DSPM, and breach protection, reducing risk at scale.
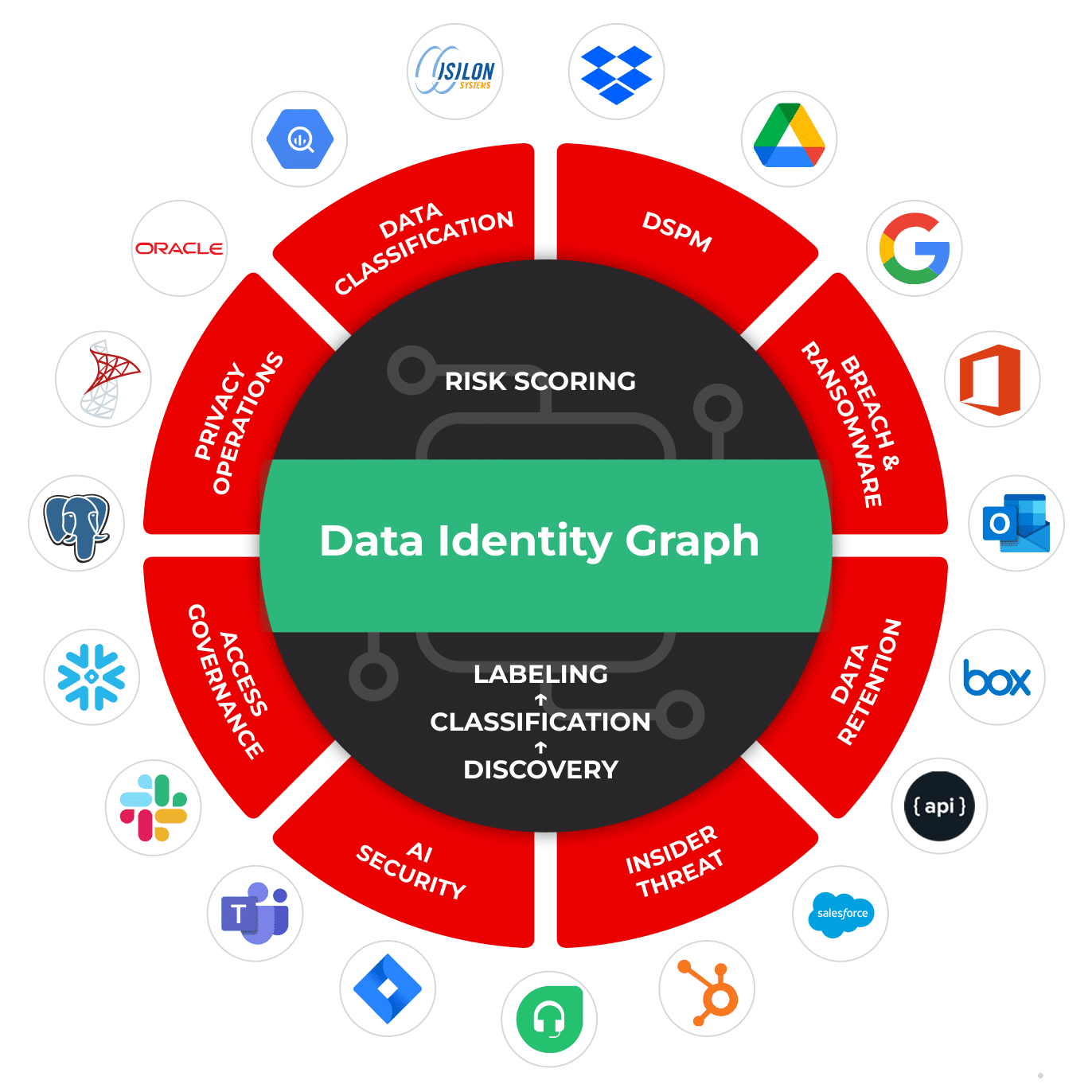
Use Cases That Turn Chaos Into Accountability
From data discovery to remediation, we give you clarity and control across your security, privacy, and governance workflows, powered by AI.
Data Security Posture Management
Discover and classify structured and unstructured data, surface risk and reduce exposure at scale.
Learn MoreData Access Governance
Enforce least privilege by ensuring only the right people access the right data, with full context.
Learn MorePrivacy Operations
Map personal data to people so you can automate DSRs, consent, and other privacy workflows with precision.
Learn MoreData Classification
Improve classification by using AI to understand data context, not just patterns or keywords.
Learn MoreBreach & Ransomware
Prevent breaches & ransomware by spotting abnormal behavior, mapping data exposure, and enforcing least privilege.
Learn MoreData Retention
Automate retention policy enforcement to reduce legal liability, breach risk, and storage costs.
Learn MoreInsider Threat
Boost DLP accuracy by applying native labels through precise data discovery and classification.
Learn MoreAI Security
Lock down sensitive data before Copilot and AI tools can expose it to the wrong eyes.
Learn More
"They have been very helpful with getting everything set up and have gone above and beyond to meet the needs of our organization and security posture. They continue to make changes and improvements based on feedback."
Manager, Legal and Compliance
Education
Compliance Accelerated
Proving compliance shouldn’t slow you down. We enforce regulations with automated data security controls, streamlined privacy workflows, and enforcement of compliance requirements.
Why Leaders Choose Lightbeam
99 %
Data discovery accuracy
40 %
Reduction in data security TCO

“Lightbeam can cover 90% of processes we were doing with four different tools… Productivity dramatically improved and our team’s time can be used for more mission critical responsibilities and less manual work.”
Key Resources & Upcoming Events

Upcoming Event
IAPP Privacy. Security. Risk. 2025
IAPP Privacy. Security. Risk. focuses on the intersection of technology, privacy, artificial intelligence governance and cybersecurity law. Visit Lightbeam at booth #219
Blog
Why Your Risk Score Should Be Your First Security Metric
Security teams are burning out. Not because they lack skill, strategy, or commitment, but because they're stuck fighting a rigged game.
Report
Unlocking the Power of AI
AI fuels growth, but 72% cite data exposure as the top risk, demanding better security, governance, and privacy controls.