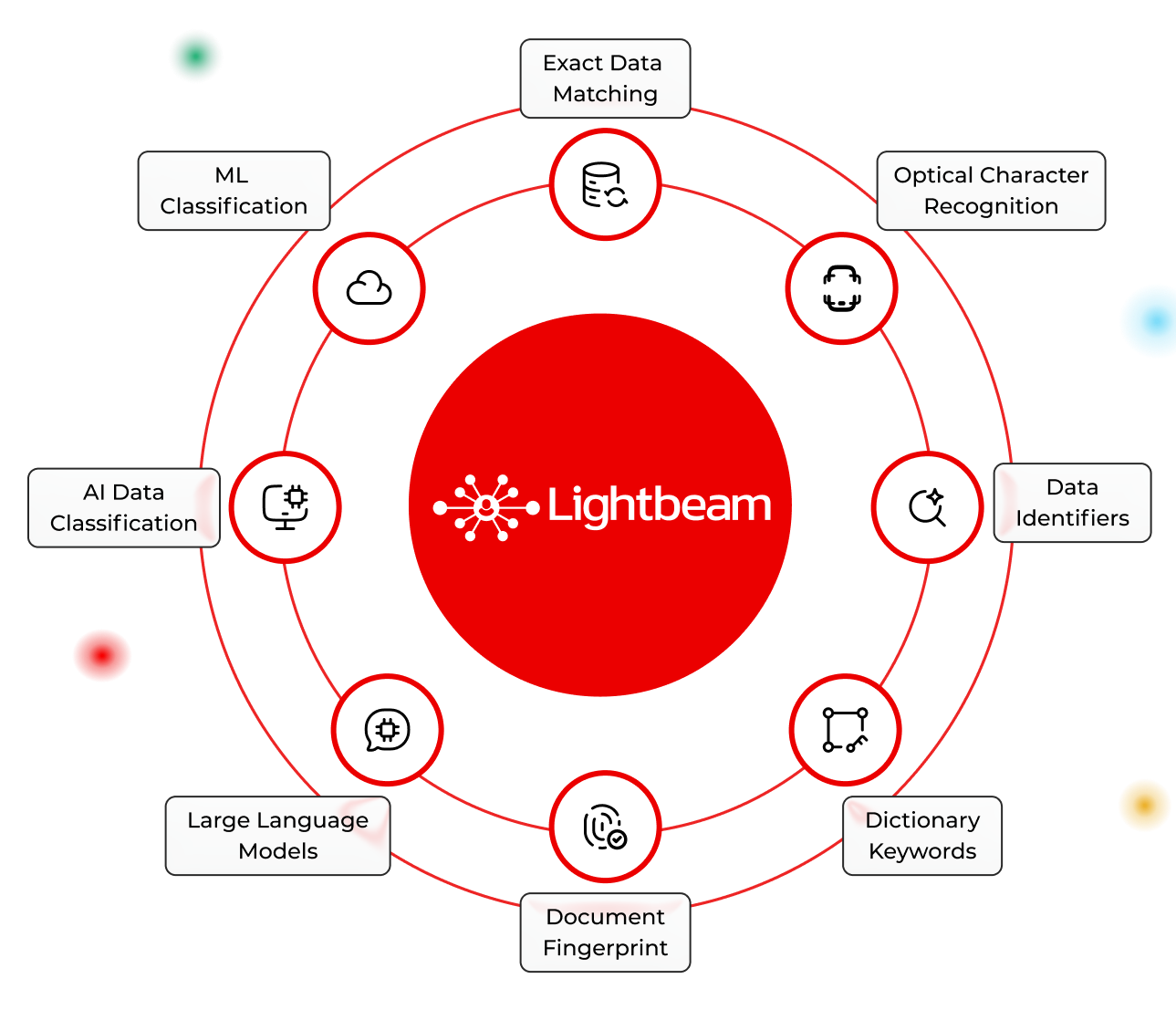
Overview
Next-Generation Data Classification
Our identity-centric classification links data to the people and context it belongs to, providing unmatched accuracy, automation, and actionable insights.
The Lightbeam Advantage
-
Identity-Centric Context
Classify what the data is, and whose, with the Data Identity Graph.
-
Custom attributes + out‑of‑box labels, day one
Detect custom attributes and apply PCI/PII/PHI labels on day one.
-
Deep coverage, no blind spots across formats
Scan structured, unstructured, BLOBs, compressed files, continuously.
-
Generate your own classifications, enforced at scale
Create categories with AI, tailor to policy, and enforce at scale.
Traditional Industry Approach
-
Regex‑first, brittle outcomes and maintenance
Static patterns miss nuance and identities; teams drown in false positives and noise.
-
Content without context or identity awareness
Labels ignore who owns the data or who can access it, so nothing meaningful changes.
-
Silos and 'best‑effort' accuracy across tools
Point tools lack accuracy and demand manual cleanup.
-
Coverage gaps across cloud, SaaS, and SMB shares
Cloud, SaaS, and SMB blind spots persist, leaving shadow data unclassified and risky.
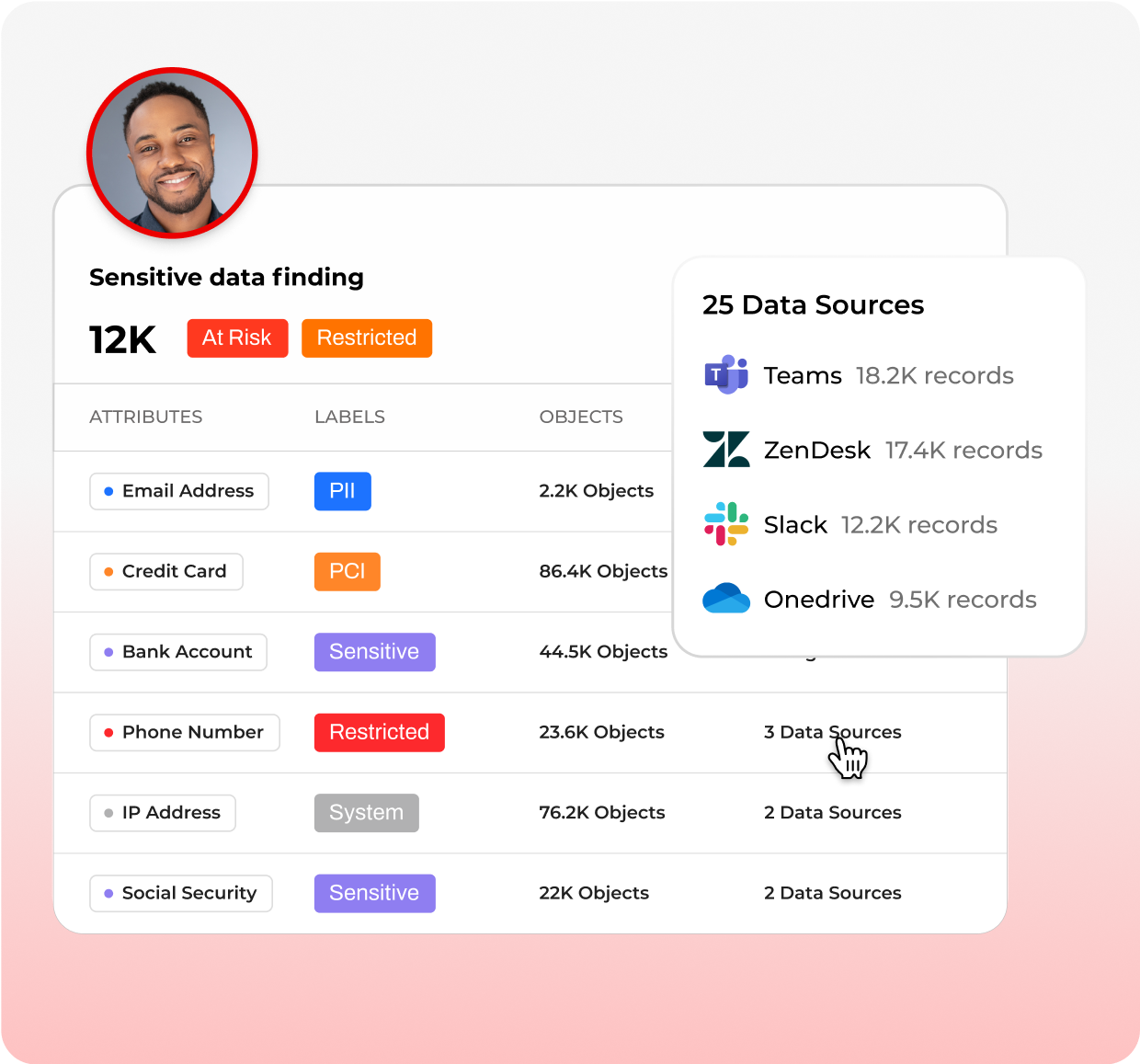
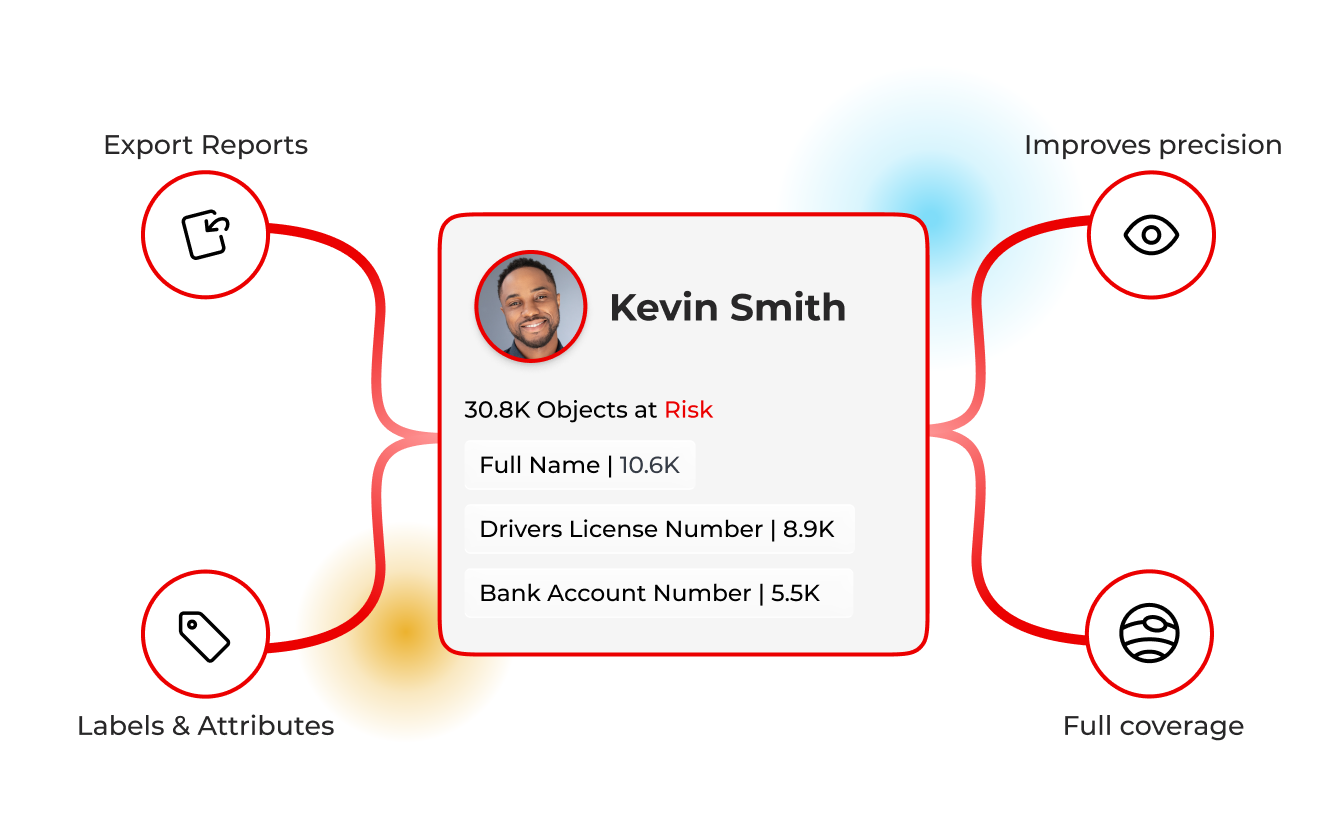
Data Classification that knows the human behind the file
See the person, not just the pattern
Lightbeam classifies by identity, content, and context, linking every attribute to real people via the Data Identity Graph. Detect PCI/PII/PHI with multilingual identifiers, add custom attributes, and apply labels across structured and unstructured data stores, including BLOBs and compressed files. Classification feeds governance, remediation, and risk scoring, so teams can act on what matters without slowing down at petabyte scale.
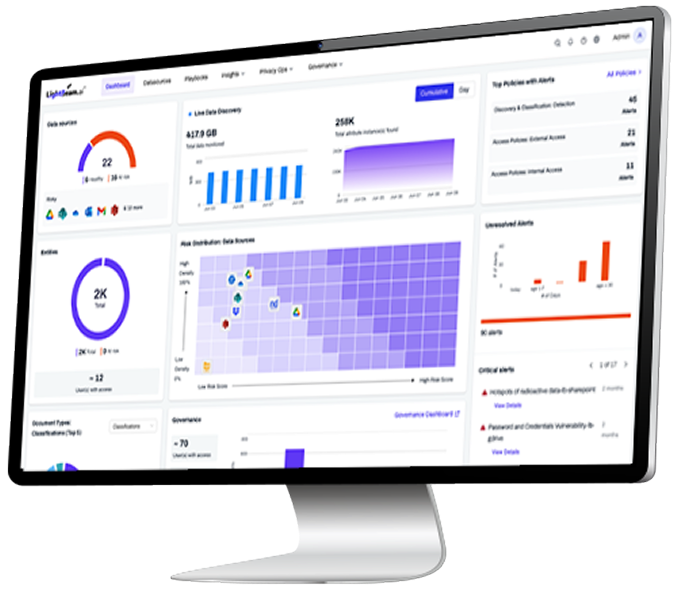
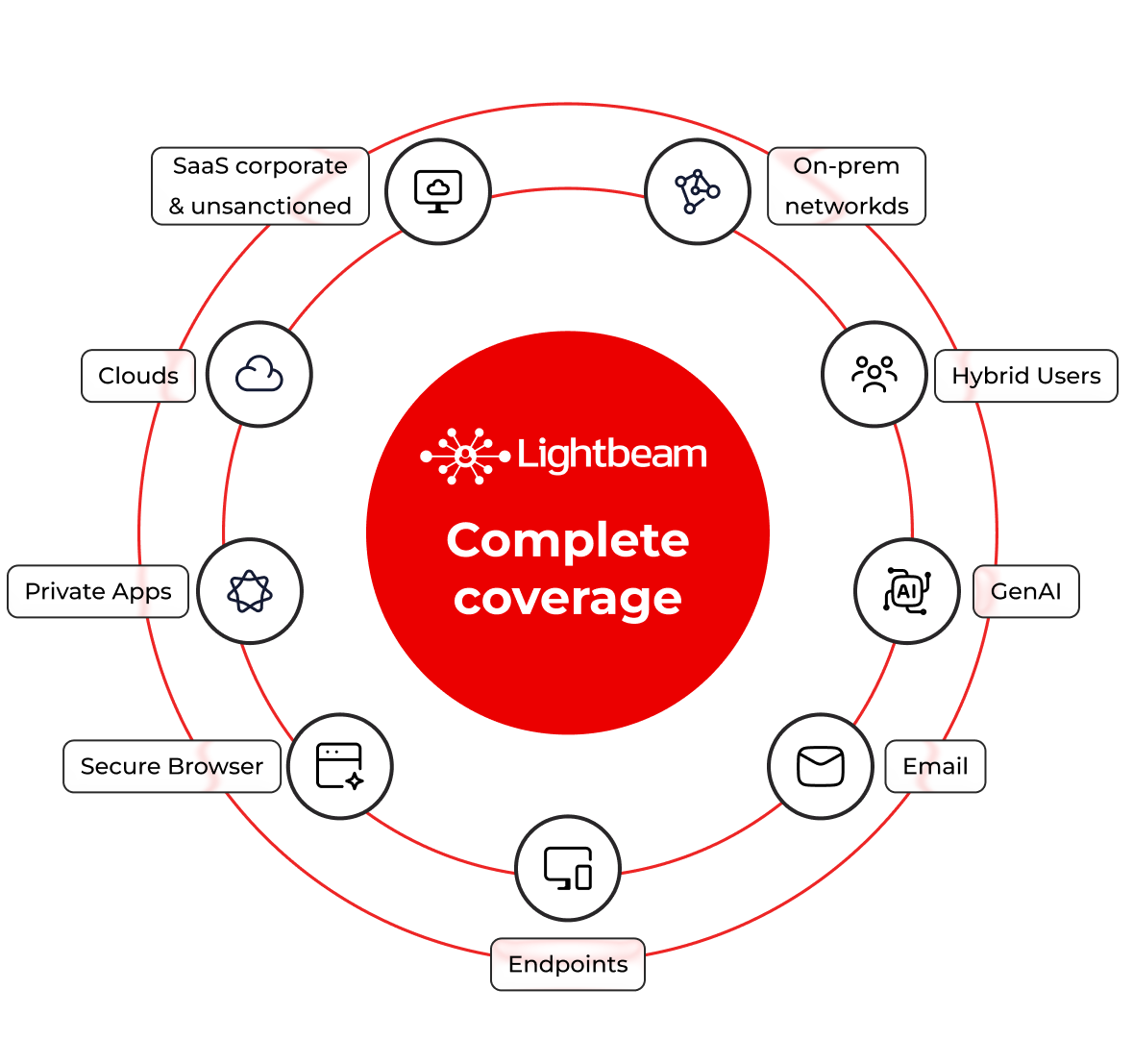
Complete coverage, built for scale
Onboard sources fast; scan databases automatically to eliminate blind spots. Navigate large files at attribute level, export object reports, and unify labels with Google and Microsoft ecosystems. Multilingual coverage rolls up into unified attributes so policies stay manageable across languages. From SMB folders to Databricks and GCS, Lightbeam keeps classification current, provable, and scalable into the petabytes.
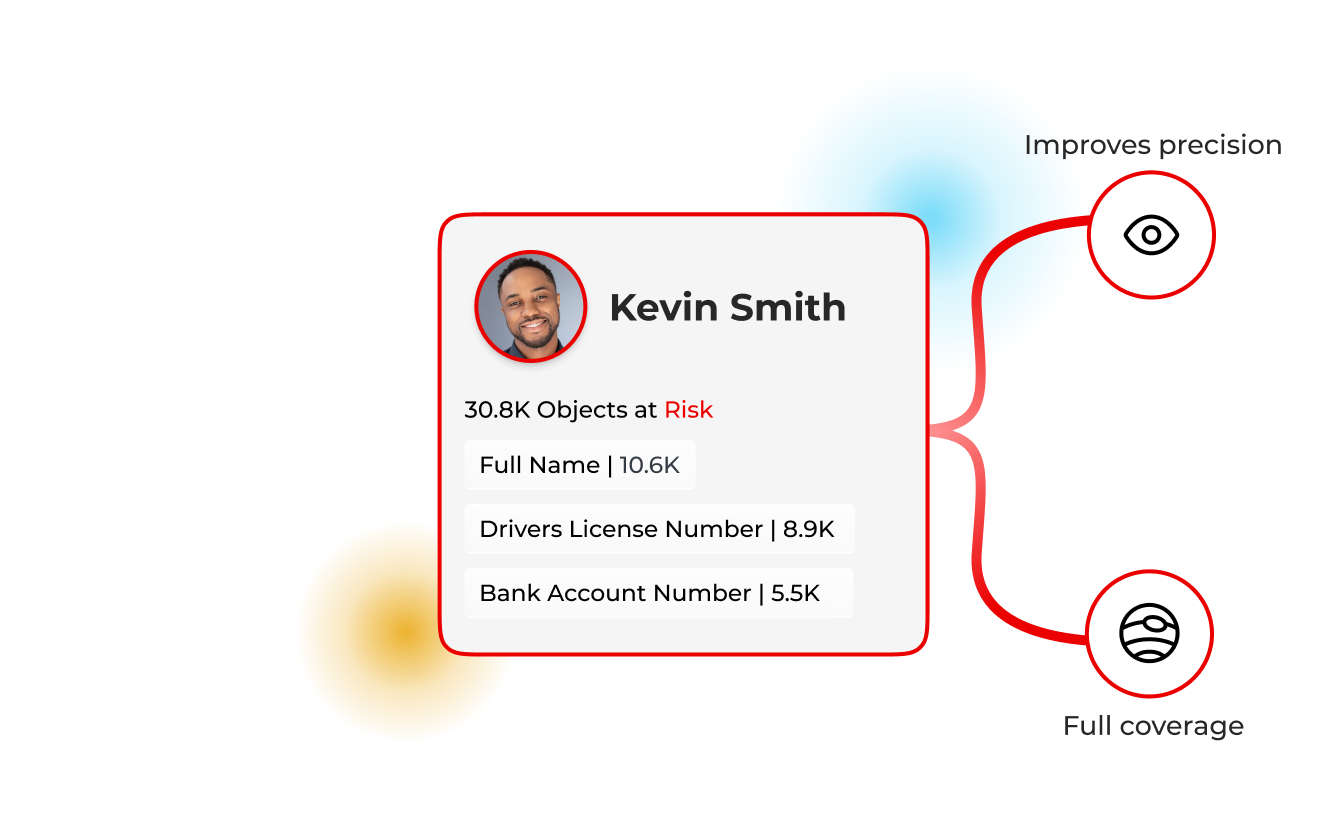
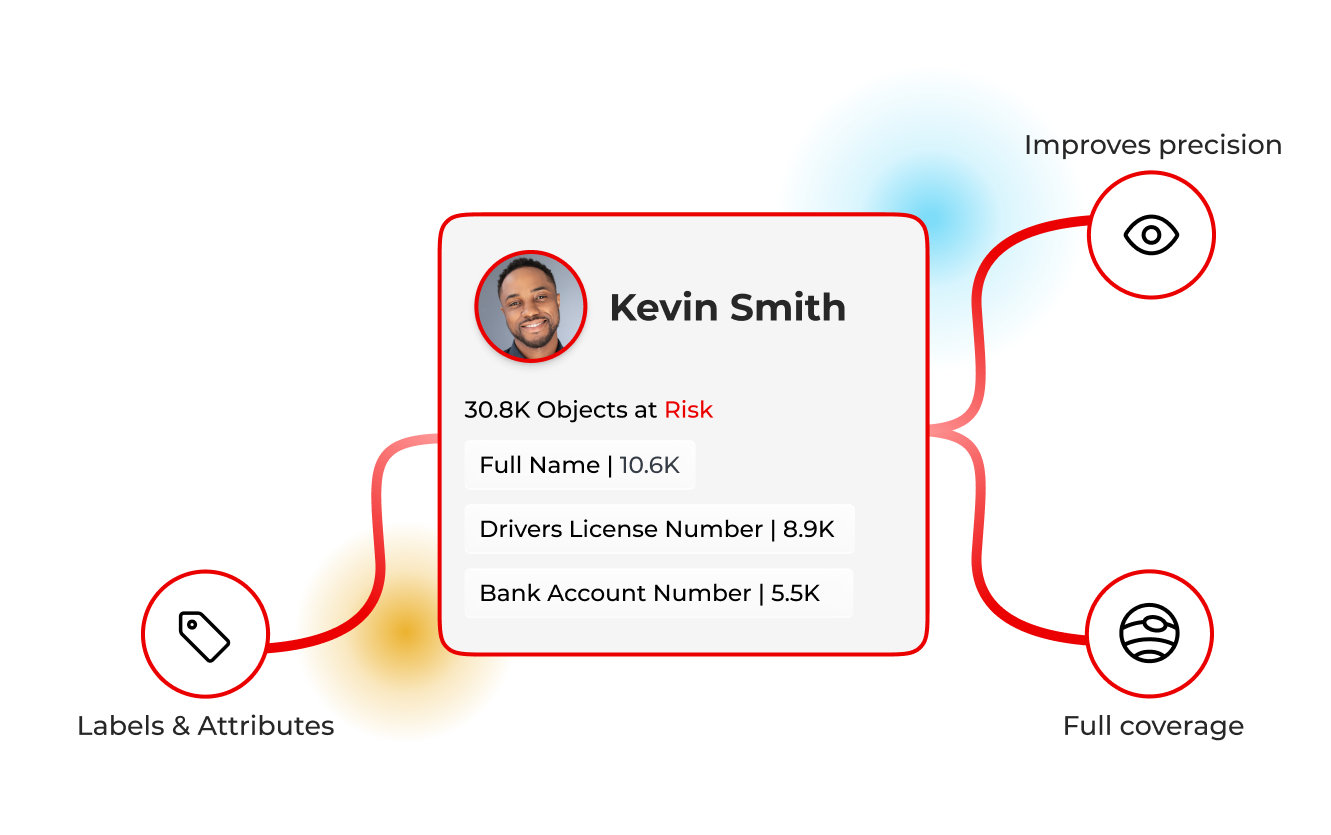
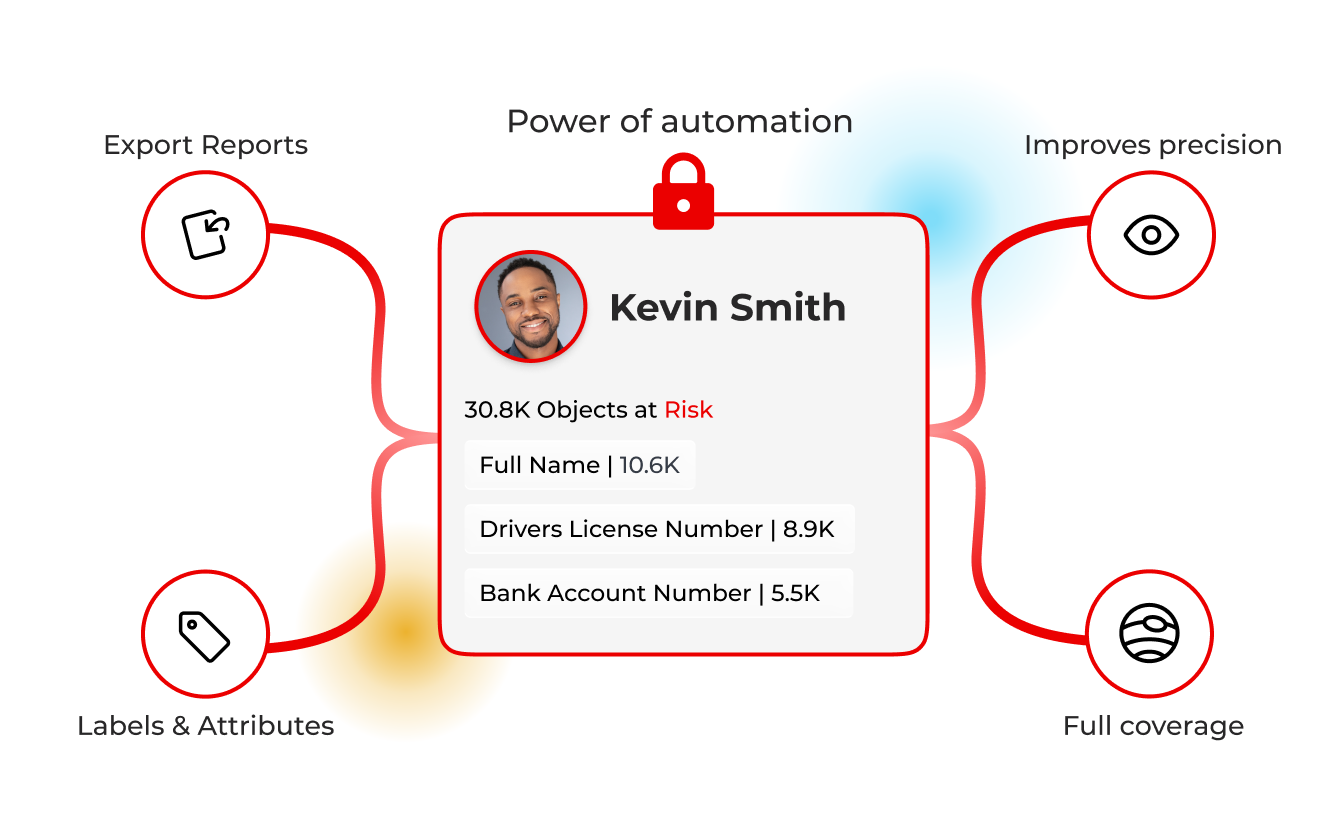
From noisy labels to identity‑centric decisions
Accuracy you can trust
Identity‑centric AI improves precision and reduces drift, customers report strong accuracy and clarity at scale.
Dive into DSPMZero blind spots
Scan structured and unstructured sources, BLOBs, compressed files, and more for full coverage.
View IntegrationsLabels that drive action
Out‑of‑box PCI/PII/PHI labels and custom attributes route into policies, playbooks, and audits.
View Automated RemediationFaster audits, fewer tools
Generate CSV object reports, align to SOC evidence, and reduce tool sprawl with one platform.
Explore Privacy OpsFrom insight to outcome
Classification powers integrated access governance, automated redaction, and risk‑based prioritization.
Close the loop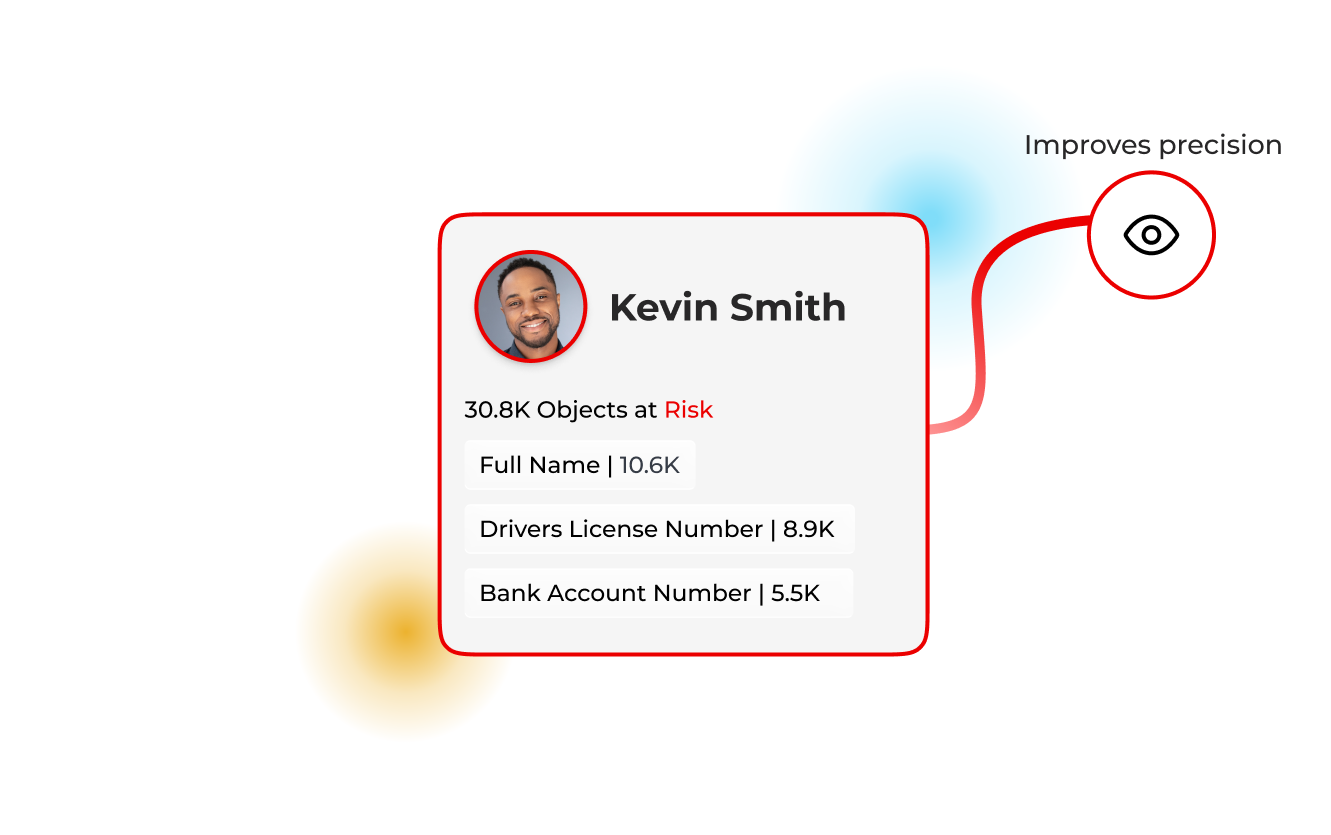
What customers say about Lightbeam Classification

“With Lightbeam, we achieved custom document classification with just one click—work that would have been prohibitively manual and expensive otherwise.”
FAQs
Frequently Asked Questions
How is Lightbeam’s Data Classification different from regex‑based tools?
Most tools tag content only. Lightbeam adds identity and access context, so you see whose data it is and who can reach it. Custom attributes, out‑of‑box labels, and wide source coverage turn categories into action for governance, privacy, and DSPM. That’s how classification drives outcomes, not noise.
Learn about Data Identity GraphWhich data sources and formats are supported for classification?
Structured databases, file shares (SMB), SharePoint, Google Drive, Databricks, SAP HANA, Confluence, Google Cloud Storage, and more—plus BLOBs, XML, Parquet, and compressed files. Future‑proof scans keep coverage current across new databases.
Explore IntegrationsCan we tailor categories to our business and automate downstream actions?
Yes. Create your own classifiers and attributes; apply PCI/PII/PHI labels; then route into policies that trigger redaction, access revocation, retention, and audit exports. Classification becomes the engine for risk scoring and governance, closing the loop.
Explore PlatformBrowse Key Resources

Blog
Summer Release 2025: Stop Ransomware Faster, Spot Insider Risk Sooner, and Prove Access is Correct