Overview
What is the Data Identity Graph?
The Lightbeam Data Identity Graph links sensitive data attributes, the identities they describe, and the users who access it, delivering context for precise security, governance, and compliance.
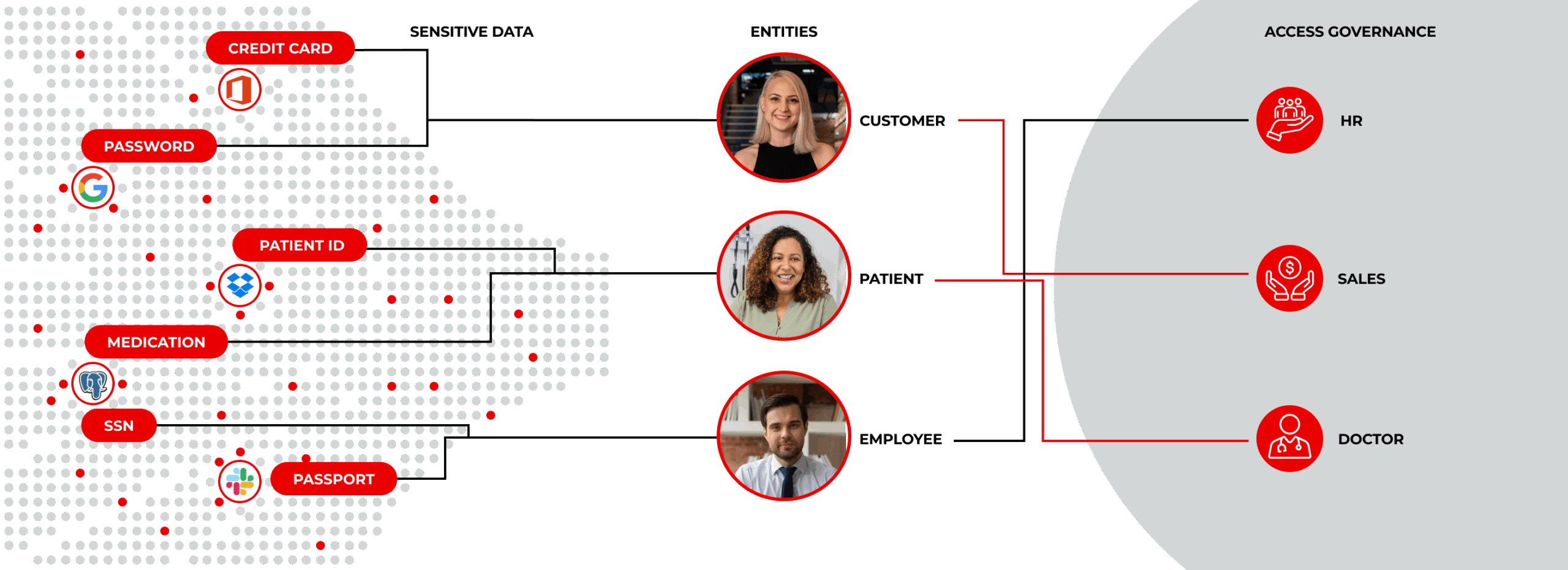
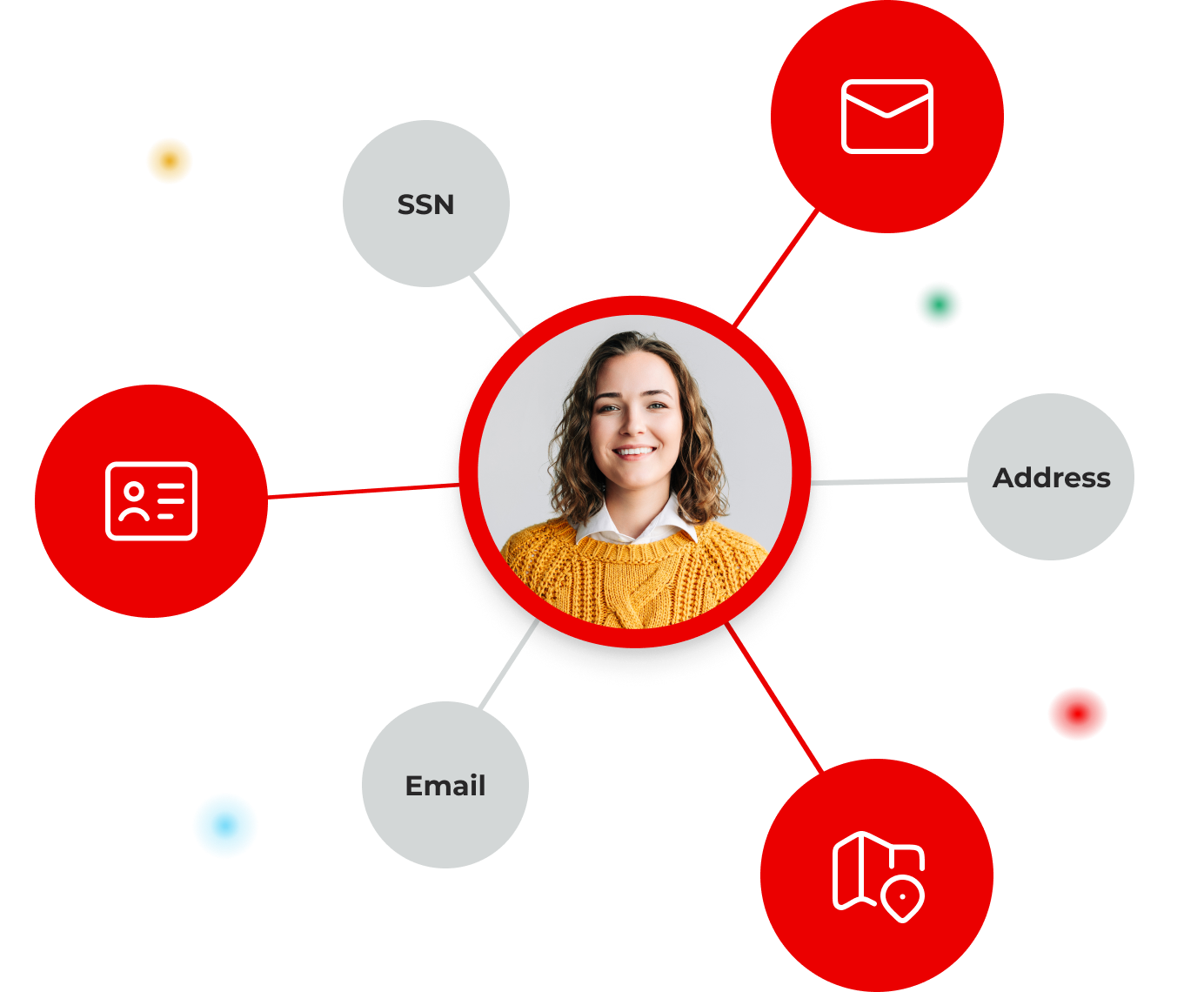
Map Data to Real Identities
Connect every file or record to the customer, employee, or partner it contains for precise classification and protection.
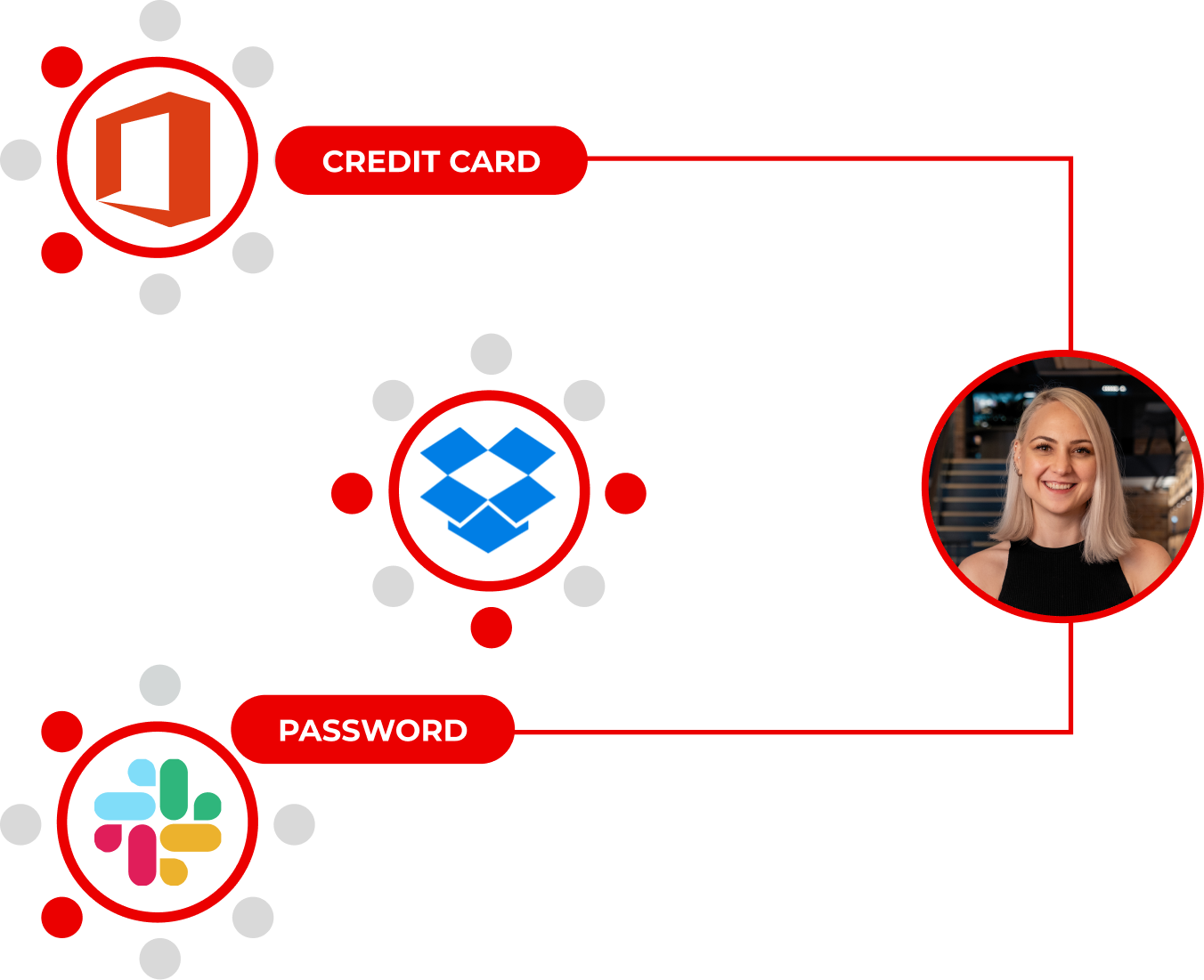
Visualize and Manage Access Paths
See who can access sensitive data, how they got access, and track usage history to detect risks.
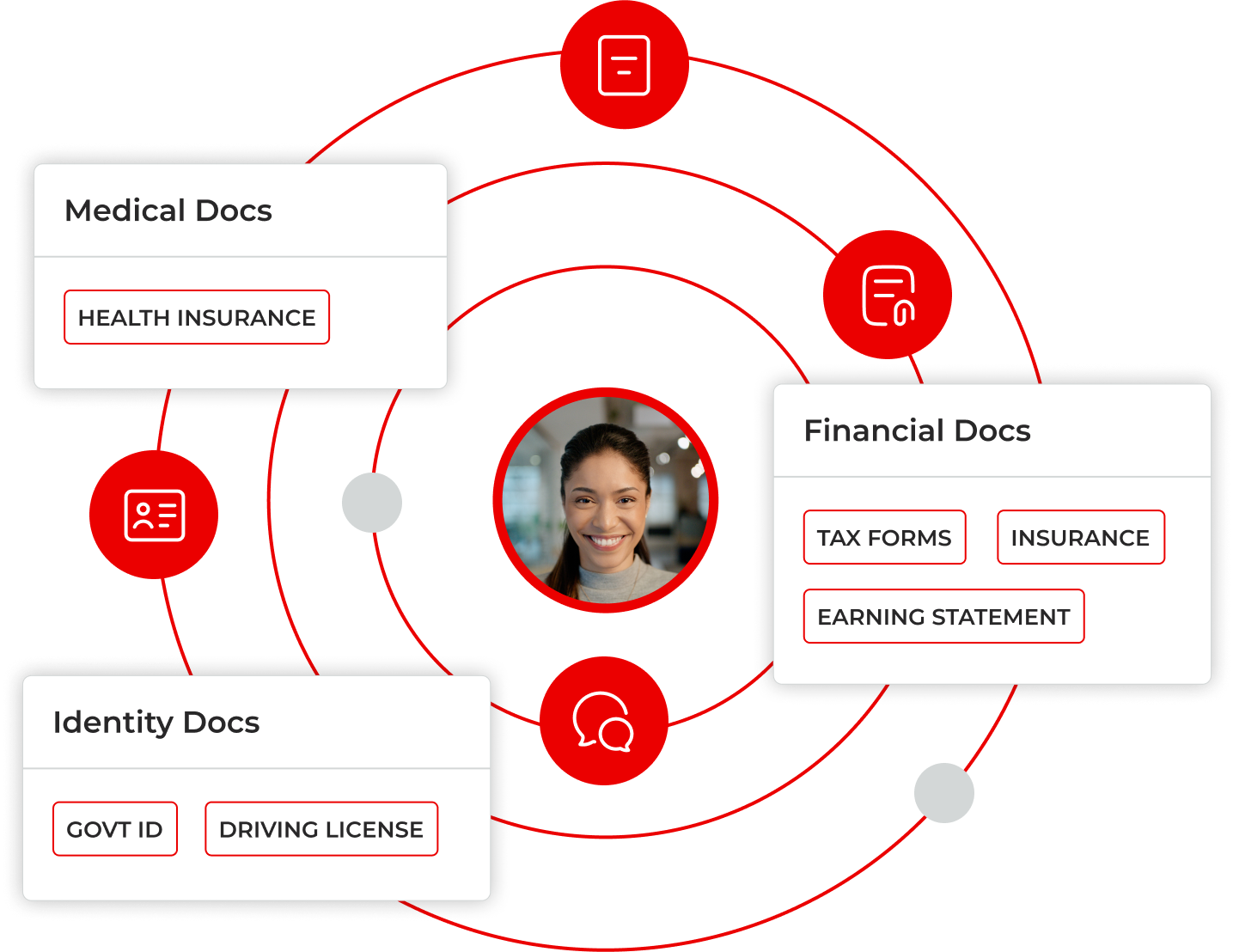
Pinpoint and Remediate Threats
Identify high-risk situations based on data sensitivity, user access, and relationships, then remediate automatically.
AI-Powered Intelligence for Precise, Context-Aware Data Security
Advanced AI, ML, and entity resolution create an unparalleled, identity-aware view of sensitive data and access.
At the core of Lightbeam’s Data Identity Graph is a sophisticated AI/ML pipeline that extracts, classifies, and links sensitive data to the identities it describes and the people or systems that can access it. Using advanced entity resolution, the platform merges fragmented data into accurate identity profiles, even across structured, unstructured, and semi-structured sources. The result: precise, context-rich risk detection and remediation.
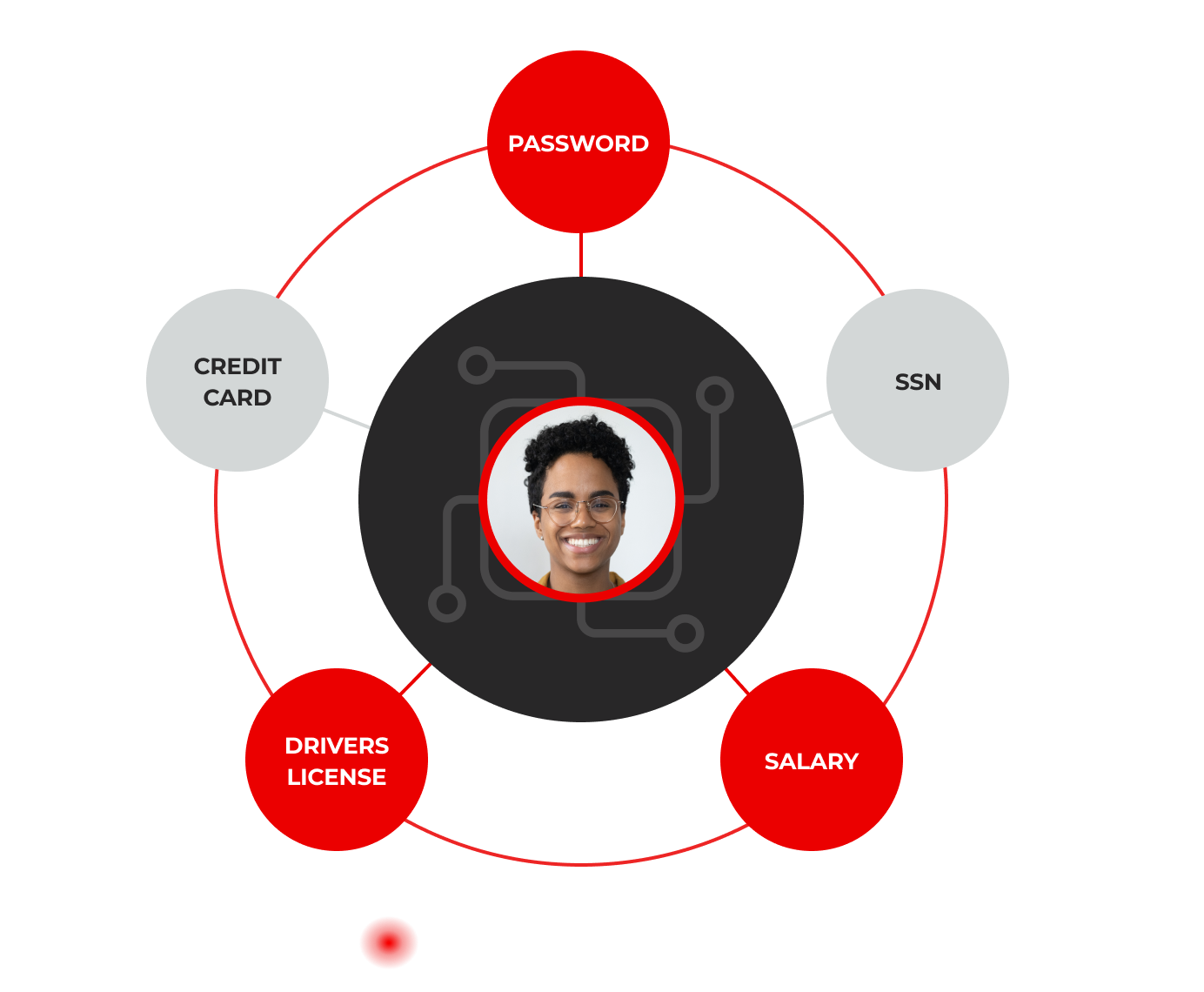
Entity Resolution That Understands Data Relationships at Scale
The Lightbeam entity resolution engine applies sensitivity, cardinality, and context rules to connect attributes, like SSNs, emails, and addresses, to the right individuals, organizations, or devices. By mapping these relationships globally and locally, the platform detects hidden risks, removes false positives, and enables policy enforcement that is both highly accurate and fully automated across your environment.
Advanced AI and Entity Resolution Power Identity-Centric Security
Entity Resolution Engine
Connects fragmented attributes like SSNs, emails, and addresses to the correct individuals or organizations, enabling accurate identity mapping across all data sources.
NLP for Sensitive Data
Uses advanced natural language processing to detect and classify sensitive data, even in unstructured documents, chat logs, or AI-generated content.
LLM-Powered Context
Leverages large language models to understand business context, reducing false positives and prioritizing risks based on data relevance.
RAG for Policy Precision
Retrieval-augmented generation delivers precise, policy-aligned responses for data discovery, access governance, and compliance workflows.
Real-Time Risk Scoring
Continuously evaluates data sensitivity, identity relationships, and access patterns to assign dynamic risk scores and trigger automated remediation.
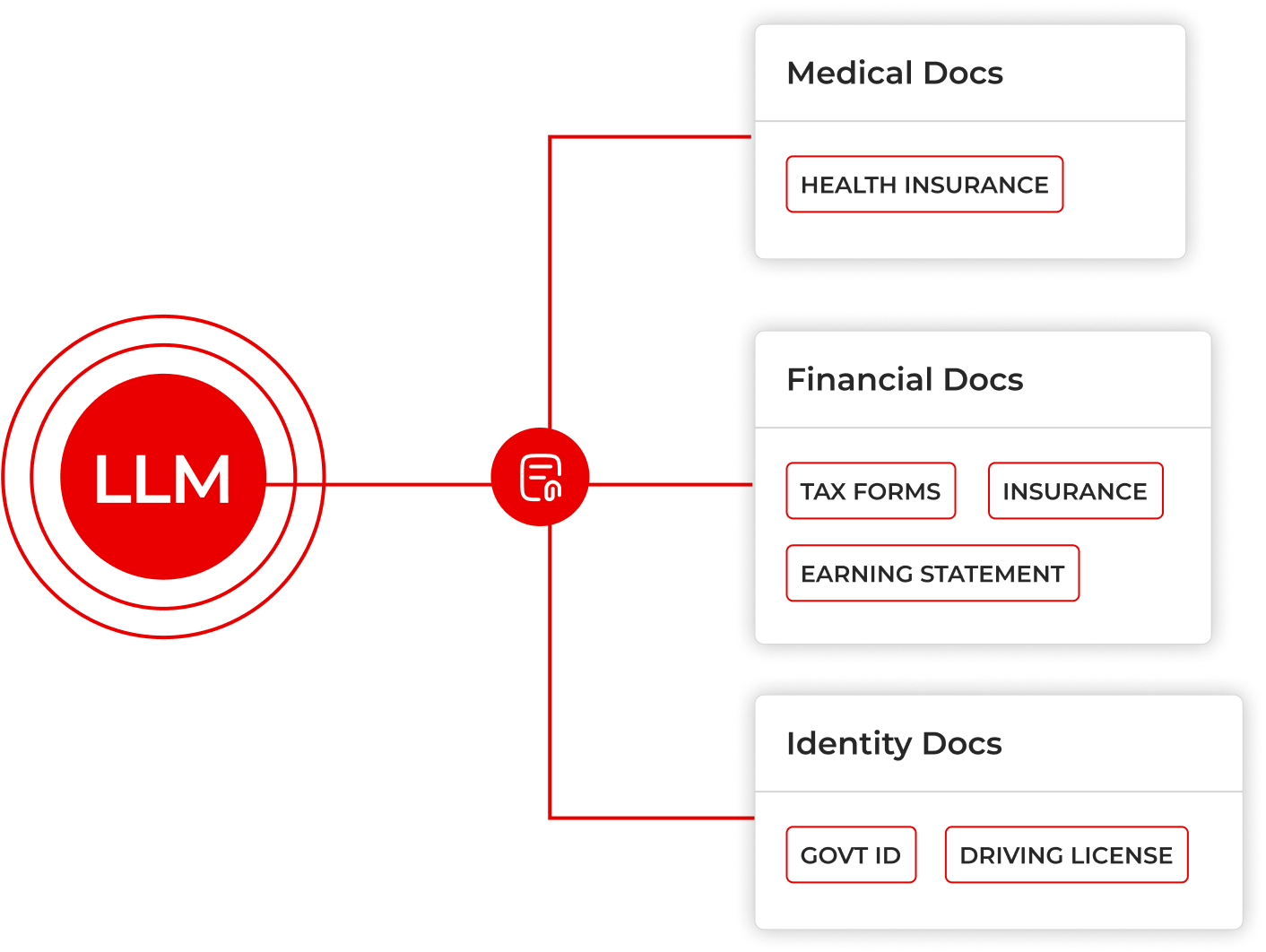

How Customers Use the Data Identity Graph
Everything You Need to Know About the Data Identity Graph
Technology FAQs
How is Lightbeam’s discovery different from regex-based tools?
Regex-based discovery relies on static patterns and keywords, often producing false positives and missing sensitive data in complex contexts. The Data Identity Graph uses AI, NLP, and entity resolution to link data to real-world identities, understand its business context, and accurately classify it across structured, unstructured, and semi-structured sources.
Explore PlatformCan the Data Identity Graph handle unstructured data?
Yes. The Data Identity Graph is designed to process structured, semi-structured, and unstructured data. Using NLP and AI, it can identify sensitive information inside documents, images, chat logs, and other formats, then map it to the individuals or entities it describes for precise risk detection and governance.
Explore IntegrationsHow does the Data Identity Graph improve risk remediation?
By combining data sensitivity, identity mapping, and access history, the Data Identity Graph pinpoints the highest-risk exposures. This context allows Lightbeam to apply policy-driven automation to remediate risks instantly, revoking access, redacting sensitive content, or enforcing retention rules with confidence and speed.
Explore Risk ScoringBrowse Key Resources

Blog
How to Comply with GDPR Articles 5 & 30 Using Identity-Centric DSPM (Data Security Posture Management)